Protected Virtual Address Mode (PVAM) in 80286:
Protected Virtual Address Mode (PVAM) in 80286 – The 80286 executes a fully upward-compatible superset of the 8086 instruction set in protected virtual address mode. The PVAM operation of the 80286 processor provides memory management and protection mechanisms and associated instructions.
The 80286 enters into protected virtual address mode from real address mode when the PE (Protection Enable) bit of the machines status word is set with the execution of LMSW (Load Machine Status Word) instruction. This operating mode also provides extended physical and virtual memory address space, memory protection mechanisms and new operations to support operating systems and virtual memory.
In this mode, 80286 provides a 1-gigabyte virtual address space per task mapped into a 16-megabyte physical address space defined by the address pin A23-A0 and B̅H̅E̅. The virtual memory address space must be larger than the physical address space since any use of an address that does not map to a physical memory location will cause a restartable exception.
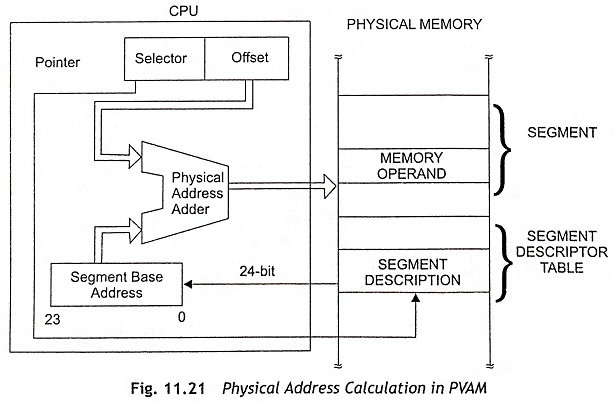
The protected mode uses a 32-bit pointer which consists of 16-bit selector and 16-bit offset components. The selector specifies an index into a memory resident table rather than the upper 16 bits of a real memory address. The 24-bit base address of the desired segment can be obtained from the tables in memory. The 16-bit offset will be added to the segment base address to form the physical address. Figure 11.21 shows the memory addressing in PVAM. The segment descriptor tables ate referenced by the CPU whenever a segment register is loaded with a selector. The memory-based tables hold 8-byte values called descriptors.
Descriptors Descriptors state how to use the memory by the 80286 processor. Some special types of descriptors are used to define new functions for transfer of control and task switching. The 80286 has segment descriptors for code, stack and data segments. This processor also has system control descriptors for special system data segments and control transfer. operations. In this section, code and data segment descriptors, system segment descriptors, gate descriptors, segment descriptor cache registers are explained.
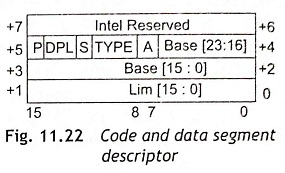
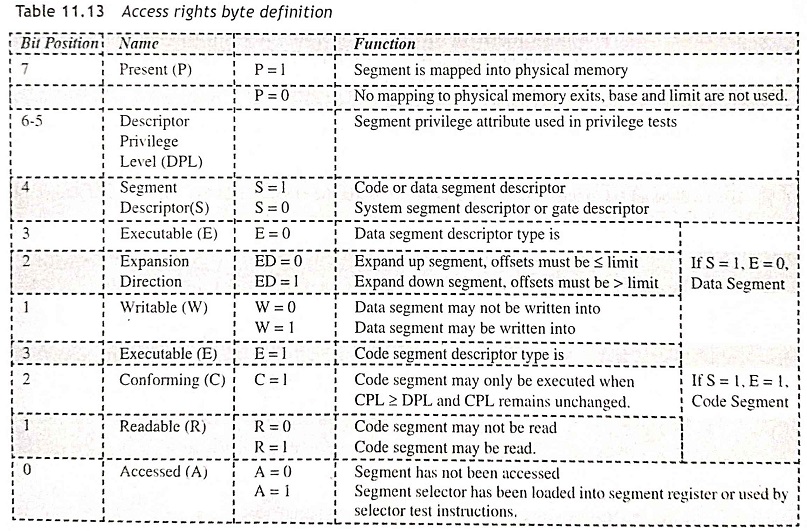
Code and Data Segment Descriptors (S = 1) The code and data segment descriptors contain segment base addresses, segment attributes including segment size up to 64 KB; access rights such as read, read/write, execute and execute/read; and presence in memory for virtual memory system. Figure 11.22 shows the code and data segment descriptors and access-rights byte definitions are illustrated in Table 11.13.
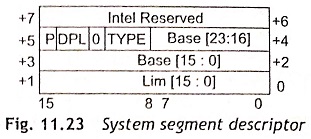
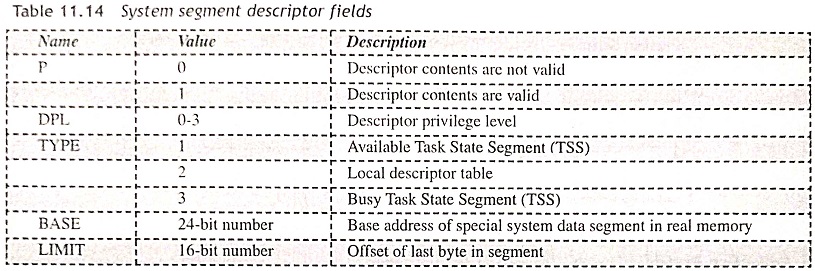
System Segment Descriptors (S = 0, TYPE = 1-3) The protected mode 80286 states the system segment descriptors which contain a table of descriptors (Local descriptor table descriptor) and segments which holds the execution state of a task (task state segment descriptor). Figure 11.23 shows the system segment descriptor and system segment descriptor fields are given in Table 11.14. This descriptor consists of 24-bit base address of the segment and 16-bit limit. The access byte defines the type of descriptor, its states and privilege level. Bit 4 of the access byte is always 0 to indicate the system control descriptor. The functions of P, DPL and Type (1-3) are given in Table 11.14.
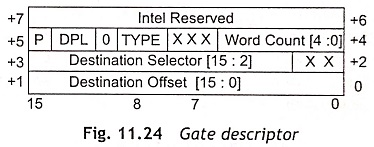
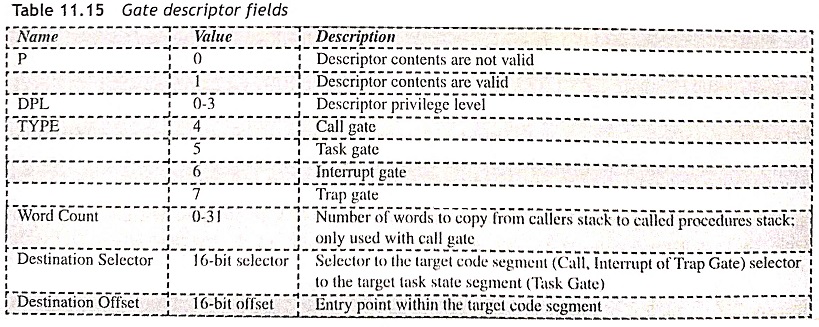
Gate Descriptors (S = 0, Type 4-7) The gate descriptors are used to control the access to entry points within the target code segment. There are four types of gate descriptors such as call gates, task gates, interrupt gates and trap gates. The gate descriptors provide information regarding indirection between the source and the destination of control transfer. Call gates are used to change privilege levels. Task gates are used to perform a task switch. The interrupt and trap gates are used to specify interrupt service routines. Figure 11.24 shows the gate descriptor and the gate descriptor fields are depicted in Table 11.15. The gate descriptor consists of a 16-bit destination selector, 16-bit destination offset and access byte format. The operation of access byte format is given in Table 11.15.
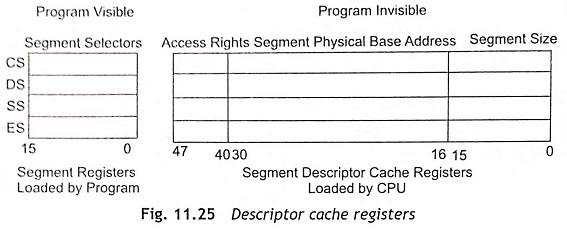
Segment Descriptor Cache Registers Figure 11.25 shows the segment descriptor cache register which is assigned to each of the four segments registers, i.e., CS, DS, SS, and ES. The segment descriptors are automatically loaded into a segment descriptor cache register, whenever the associated segment register is loaded with a selector. Once segment descriptors are loaded into segment descriptor cache registers, the segment of memory uses the cached descriptor information instead of accessing the descriptor. The segment descriptor cache registers are invisible to programs.
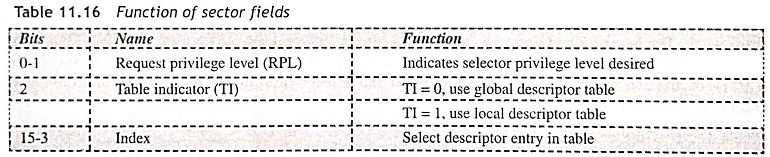
Selector Fields In the protected mode of 80286, the selector has three fields such as descriptor entry index, local or global descriptor table indicator (TI), and selector privilege (RPL) as shown in Fig. 11.26. The first two bits D1-D0 are called requested privilege level RPL field. The D2 bit states the descriptor table type. The index D15-D3 bits are used to indicate descriptor base in the descriptor table. The function of the fields is given in Table 11.16.
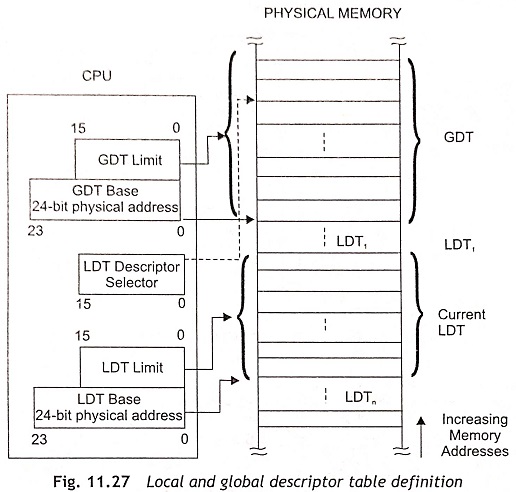
Local And Global Descriptor Tables The local and global descriptor tables contain all descriptors accessible by a task at any given time. Actually, a descriptor table is a linear array of up to 8K (8192) descriptors. The upper 13 bits of the selector field are an index into a descriptor table. Each descriptor table has a 24-hit base register to locate the descriptor table in physical memory and it has a 16-bit limit register which confines descriptor access to the defined limits of the table. Figure 11.27 shows the local and global descriptor tables.
The Global Descriptor Table (GDT) contains descriptors available to all tasks. The Local Descriptor Table (LDT) contains descriptors that can he private to a task. All tasks may have their private LDTs. The GDT may contain all descriptor types except interrupt and trap descriptors. The LDT contains segment, task gate, and call gate descriptors. A segment cannot be accessed by a task if its segment descriptor does not exist in either GDT or LDT at the time of access.
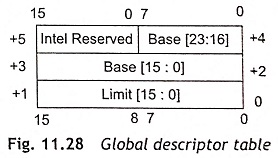
The LGDT (Load Global Descriptor Table) and LLDT (Load Local Descriptor Table) instructions load the base and limit of the GDT and LDT. The LGDT and LLDT are privileged, and these instructions may only be executed by programs at privilege level 0. The LGDT instruction loads a six-byte field containing the 16-bit limit and 24-bit physical base address of the GDT as depicted in Fig. 11.27. The LLDT instruction loads a selector which refers to an LDT descriptor containing the base addresses and limit as shown in Fig. 11 28
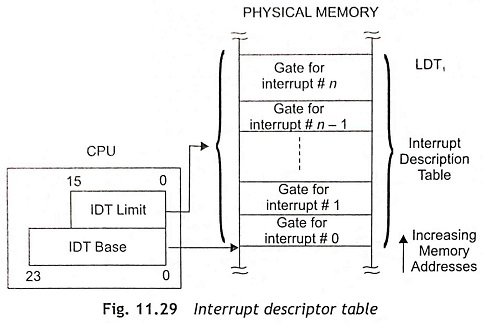
Interrupt Description Table In the protected mode, the 80286 processor has a third descriptor table known as interrupt Descriptor Table (IDT). The IDT can be used to define up to 256 interrupts. Figure 11.29 shows the Interrupt Descriptor Table. The IDT contains task gates, interrupt gates and trap gates. The IDT has a 24-bit physical base and a 16-bit limit register in the CPU. The privileged LIDT (Load Interrupt Descriptor Table) instruction loads these registers with a 6-byte value in same way of the LGDT instruction. Usually, the IDT entries are made through INT instructions, external interrupt vectors, or exceptions. The IDT should have 256 bytes in size to allocate space for all reserved interrupts.
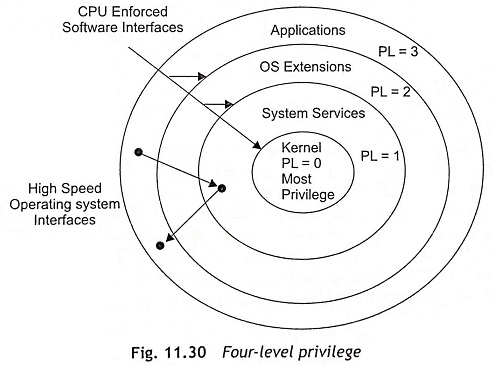
Privilege The 80286 processor can support a four-level hierarchical privilege system which controls the use of privileged instructions and access to descriptors within a task. Figure 11.30 shows four-level privilege mechanism. The privilege levels are numbered 0 through 3. Level 0 is the most privileged level whereas Level 4 is the least privileged level. Privilege levels provide protection within a task. The operating system routines interrupt handlers, and other system software can he protected from unauthorized accesses within the virtual address space of each task using the four levels of privilege. Each task in the system has a separate stack for each privilege levels. Tasks, descriptors, and selectors have a privilege level attribute that can find out whether the descriptor may be used. The task privilege has an effect on the use of instructions and descriptors. The descriptor and selector privilege only effect access to the descriptor.